|
dystopian visions, political ponerology, netting, job seeking, time killing, stuff archive..
21 July, 2016
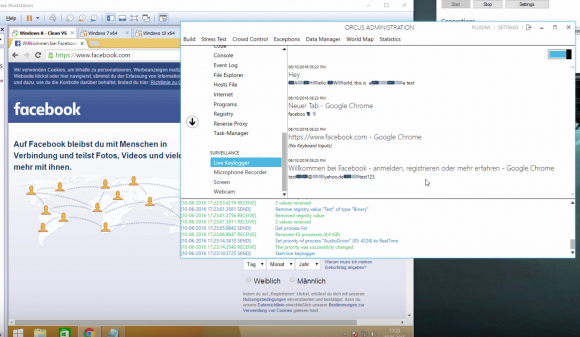
Canadian Man Behind Popular Orcus RAT
20 July, 2016
Download a Mass of 240+ Free Technical eBooks From Microsoft
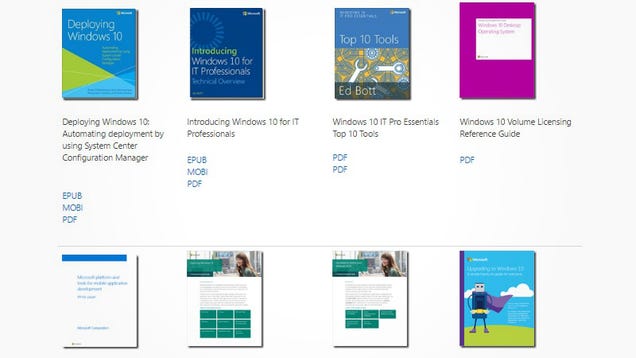
It's that wonderful time of year again. The Microsoft MSDN blog is offering another hefty collection of useful, totally free eBooks for you to download.
19 July, 2016
Flawed code hooking engines open endpoints to compromise
Six common security issues stemming from the incorrect implementation of code hooking and injection techniques have been unearthed by EnSilo researchers in over 15 different products, including anti-virus (AV) and anti-exploitation solutions, data loss prevention software (DLP) and host-based intrusion-prevention systems (HIPS). The fact that some of these issues also affect three different hooking engines, including the most popular one (Microsoft Detours), means that thousands of product are likely affected – and not just security … More →
Entire US Voters’ Registration Records Is Available Online On Dark Market For 0.5BTC Per State
It's raining confidential data on the Dark Net. It seems that every few days someone is offering data on there that wouldn't be available otherwise. Recently, we discovered a seller going by the online handle of "DataDirect" is claiming to have full access to voter registration records of the citizens of the United States and offering buyers state by state voters' records where the price for each state is 0.5 BTC (340.38 US Dollar).
A hacker is selling US voters' registration records on the Dark Net and looks like the U.S. Election Assistance Commission (EAC) has no clue!
At present, it is hard to say if the offered data is legit but the same seller is also offering Thomson Reuters World-Terrorist database on the same Dark Net Marketplace "The Real Deal."
An important fact about the data is that in December 2015 security researcher Chris Vickery found 191 million US voter registration records online in an unprotected folder however it's unclear whether the DataDirect seller downloaded the data from the same place or he stole the data from some government server. Nevertheless, another important aspect of this news is that back in December, Vickery stated that there was a lack of interest shown by the authorities in recovering the data or taking the database off from public view as
Vickery said,
"I've been working with journalists and authorities for over a week to get this database shut down or secured. No luck so far."
According to the listing's description "US voter registration records. Selling the DB on a State-by-State basis. 0.5 BTC per state (you must tell me which State you want. Some people think it's unfair to make each State cost the same amount because some States are much bigger than others. I think it's just easier this way."
Here are two screenshots shared by the seller showing sample data! The first screenshot shows personal and voting details of a native from the State of California.In order to protect user's privacy we have blurred the crucial information.
This screenshot shows state by state files in .JSON format where az stands for the state of Arizona and so on. The hacker claims to have access to voters' data from all 50 states.
By looking at the sample screenshots it seems the data is legit and if it really is, this is a massive blow to the U.S. Election Assistance Commission (EAC) and users themselves. If scammers, Chinese, Russian hackers or anyone else for that matter got access to this database you can expect a cyber 9/11 just like the ex-NSA chief claimed a couple of years ago.
18 July, 2013
Trolls' characteristicae
1) They have a lot of free time, they are mostly lonely people.
2) They often ingratiate themselves to a person or two on the group and use them to stay in the group. They may protest with these "friends" that their right to free speech is being curtailed.
3) They sometimes use "socketpuppets", i.e. fake identities that may be used to sustain, or to inflame the troll's position or theory or attack. At times the socket puppets' names are anagrams or similar to the troll name. Thus a troll may engage in artificial conversations with himself. However impersonating multiple people is frowned upon by the more able trolls and is considered the lowest of the possible troll tactics.
Yes (as somebody wrote long ago), much like hyenaes: if a messageboard is strong and vibrant, with healthy ideas and intelligent discussion among posters, then these tend to be too interested in what is going on to pay much attention to the trolls. However, once a forum begins to show signs of decay - usually due to bickering amoung the regular visitors - then the trolls run rampant and it is only a matter of time before the forum disintegrates.
Moreover: "Trolls remind us that this is not private space. Lurkers are everywhere but it is easy to forget that. Chatting away on a thread with an old buddy it is easy to reveal personal details about one's life that you might not really want public. Trolls remind us that in a public forum anyone can read what we write."
Moreover, as we have seen in Trolls and Schopenhauer and with the debunking example above, trolls DO deliver us many useful findings about "Eristic Dialectic stratagems". Findings that we can easily apply outside the world of Usenet :-)
This said, trolls and (even more) shills are very often de facto and/or de jure just lackeys of the commercial powers that be. What all trolls have in common is that they flood newsgroups with inappropriate material in an effort to suppress discussion they don't want taking place. If it were radio, you would call it "jamming" and everybody would agree it was censorship. But on Usenet or on messageboards, the effect is more subtle and the mechanism more complex (involving user interface limitations of newsreading software) so it hasn'e been widely recognized yet. Some of the most determined destroyers are professionals trollers connected to people that stand to lose if a specific Usenet newsgroup (or any given specific messageboard) proves to be a viable alternative to the(ir) controlled channels of mass communications.
Let's see how to (try to) destroy them...
(stolen without permission from Fr***a+) sorry!
21 July, 2008
Navy agrees to camouflage 'swastika' base
Dan Glaister in Los Angeles
Thursday September 27, 2007
The Guardian

Painting a swastika on a public building is a hate crime. But what happens when the building itself is the swastika? While appearing innocuous from the ground, the striking shape of a construction in San Diego, now on view to internet users accessing Google Earth, is unmistakable - it resembles the Nazi symbol.
Ground-breaking began for the six-building complex at the Coronado US navy base in southern California in 1967. While the original plans called for two central buildings and a single L-shaped barracks, Naval Amphibious Base Complex 320-325 evolved in design. By the time it was finished in 1970 it had four L-shaped buildings - set at right angles. That was when the problem was spotted.
The scheme's architect, John Mock, said this week that while he was aware of the shape as viewed from above he did not think it a true swastika. "We knew what it was going to look like, but it isn't that. It's four L-shaped buildings ... looking at it from the ground or the air, it still is."
Forgotten about after the initial controversy, the buildings' form has emerged again as an issue thanks to the internet and Google Earth. It has led an unlikely alliance - of bloggers, anti-discrimination activists, lawmakers and one talk-radio host - to take action. And now the navy has added $600,000 (£300,000) to its 2008 budget for camouflage. Landscaping, rock structures and solar panels should help disguise its shape.
"We take this very seriously," said Scott Sutherland, deputy public affairs officer for the Navy Region Southwest. "We don't want to be associated with something as symbolic and hateful as a swastika."
But the remedy may not stop conspiracy theorists. The buildings, surmise some bloggers, were put up by German POWs as a Hitler tribute. Others say that nearby buildings look like planes pointing at the swastika. One theory has it that, sideways, the buildings resemble Calvary crosses. And the crosses point to Jerusalem.

Thursday September 27, 2007
The Guardian
Painting a swastika on a public building is a hate crime. But what happens when the building itself is the swastika? While appearing innocuous from the ground, the striking shape of a construction in San Diego, now on view to internet users accessing Google Earth, is unmistakable - it resembles the Nazi symbol.
Ground-breaking began for the six-building complex at the Coronado US navy base in southern California in 1967. While the original plans called for two central buildings and a single L-shaped barracks, Naval Amphibious Base Complex 320-325 evolved in design. By the time it was finished in 1970 it had four L-shaped buildings - set at right angles. That was when the problem was spotted.
The scheme's architect, John Mock, said this week that while he was aware of the shape as viewed from above he did not think it a true swastika. "We knew what it was going to look like, but it isn't that. It's four L-shaped buildings ... looking at it from the ground or the air, it still is."
Forgotten about after the initial controversy, the buildings' form has emerged again as an issue thanks to the internet and Google Earth. It has led an unlikely alliance - of bloggers, anti-discrimination activists, lawmakers and one talk-radio host - to take action. And now the navy has added $600,000 (£300,000) to its 2008 budget for camouflage. Landscaping, rock structures and solar panels should help disguise its shape.
"We take this very seriously," said Scott Sutherland, deputy public affairs officer for the Navy Region Southwest. "We don't want to be associated with something as symbolic and hateful as a swastika."
But the remedy may not stop conspiracy theorists. The buildings, surmise some bloggers, were put up by German POWs as a Hitler tribute. Others say that nearby buildings look like planes pointing at the swastika. One theory has it that, sideways, the buildings resemble Calvary crosses. And the crosses point to Jerusalem.
Blogged with the Flock Browser
Subscribe to:
Posts (Atom)